Information Asset Management System Contact Us
Build a unified information asset management system that integrates different types of critical information assets, providing organizations with control over the essential Information Asset Management System (IAMS). During organizational development, key information assets include software, hardware, and information categories. Their management and control are vital aspects of current information security controls. Understanding various asset conditions helps managers deploy proactively.
Traditional Information Security Management System (ISMS) implementation relies on documents and forms for inventory and control. This causes inconvenience as electronic files cannot set "minimum access privileges" and hinders information search and statistical operations.
The Information Asset Management System developed by ISCOM helps organizations control asset lifecycles through asset value assessment and risk evaluation, developing risk treatment plans for high-risk assets with various control measures to ensure comprehensive protection of critical information assets.
Product Features

Information Management
Unified management of information asset resources, controlling internal asset lifecycles (software, hardware and other assets).

Application Forms
Replace paper-based application forms with electronic approval process for software asset requests.

Inventory Operations
Routine inventory operations, recording and tracking historical inventory changes, complying with information security control mechanisms.

Data Center Management
Manage IT asset outsourcing vendor members and contract deliverables.

Vulnerability Scan Management
Provides vulnerability scan report upload, patch result reporting and status control management.

System Assistance Management
Assigns information contact windows by department for inventory coordination and case dispatch.

Information Management
Unified management of information asset resources, controlling internal asset lifecycles (software, hardware and other assets).

Application Forms
Replace paper-based application forms with electronic approval process for software asset requests.

Inventory Operations
Routine inventory operations, recording and tracking historical inventory changes, complying with information security control mechanisms.

Data Center Management
Manage IT asset outsourcing vendor members and contract deliverables.

Vulnerability Scan Management
Provides vulnerability scan report upload, patch result reporting and status control management.

System Assistance Management
Assigns information contact windows by department for inventory coordination and case dispatch.
Cross-domain Professional Capabilities  Central Taiwan's Leading IT Service Provider
Central Taiwan's Leading IT Service Provider
Flexible Functional Architecture
- Provides various asset management based on organizational industry characteristics.
- Module functions can be expanded according to needs and adjusted based on unit requirements.
- Function usage is controlled by unit or role to ensure minimum access privileges.
Resource Integration Management
- Through the Information Asset Management System, monitor all internal organizational asset usage for better resource utilization and adjustment.
- If units already have asset management systems, such as property management systems or employee AD, data can be integrated through external system interfaces, enabling organizations to share existing system data.
Service Architecture
Through the Information Asset Management System, we provide three major functional architectures: asset updates, asset management, and asset inventory, enabling unified centralized control of internal organizational information assets with system data integration for improved efficiency. Additionally, it facilitates routine Information Security Management System (ISMS) audit operations.
The Information Asset Management System uses modular function development, providing flexible function modules and customized risk assessment operations based on organization type and information security consultant team requirements. This helps organizations effectively control critical information assets and establish organizational risk control measures to reduce the likelihood of security incidents.

Application Forms
Add
Transfer
Decrease
Increase
Electronic Form Process

Data Integration
HR Management System
Financial Management System

ISMS Categories
Software
Information
Personnel
Hardware
Services
Facilities

Resource Management
Account
PC
IP/DNS
Firewall

Regular Inventory
ISMS Inventory and Risk Assessment
Personal Information Inventory and Risk Assessment
Protection Requirements Level Assessment

Irregular Inventory
Vulnerability Scan Report Management
Host Vulnerabilities
Web Vulnerabilities
Resource Inventory Items
Account
Personal Computer
IP/DNS
Firewall
Critical Assets Often Overlooked - ISCOM's Professional Team Helps You Safeguard
Organizations and enterprises often overlook certain information assets that actually require enhanced protection to prevent unauthorized access, use, disclosure, modification, destruction, or theft by malicious actors, which could lead to irreversible losses for the organization or enterprise.
The commonly overlooked critical information assets can be divided into five major categories: Data Center Hardware Equipment Quantity, Software System Risk Levels, Project Contract Legal Documents, Personally Identifiable Information (PII), and Human Resource Task Allocation Status.


Data Center Hardware Equipment Quantity
Management of data center equipment capacity and rack mounting operations.
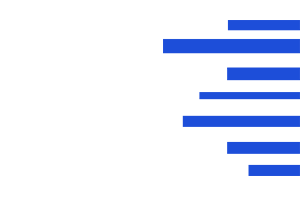

Software System Risk Levels
Provides organizational information system risk levels based on high,
medium, and normal risk categories, ensuring appropriate risk control measures.



Project Contract Legal Documents
Control of physical and electronic storage locations for trade secrets content
related to customer and supplier cooperation.


Personal Identifiable Information (PII)
Basis for personal data collection, processing, and utilization,
along with specific purpose control.



Human Resource Task Allocation Status
Standard Operating Procedures (SOP) for critical service processes,
ensuring proper handover and attention points for service and personnel assets.




